Encryption vs Hashing in SC-900
Data protection is a core theme in SC-900 (Microsoft Security, Compliance, and Identity Fundamentals), and one of the most commonly misunderstood topics is the difference between encryption and hashing.
Many beginners assume these two concepts are interchangeable.
They are not.
SC-900 does not expect you to implement cryptographic algorithms or configure keys. Instead, it tests whether you understand what encryption and hashing are used for, how they differ, and why both are important in modern security.
This article explains Encryption vs Hashing in SC-900 clearly, without unnecessary technical depth.
Why SC-900 Covers Encryption and Hashing
Modern environments handle massive amounts of sensitive data:
- User credentials
- Emails and files
- Application data
- Compliance-sensitive information
Protecting this data is critical.
SC-900 introduces encryption and hashing because they are foundational security concepts used across identity, compliance, and data protection.
Understanding these basics helps you:
- Interpret security decisions
- Understand compliance requirements
- Avoid common misconceptions in interviews and exams
What Is Encryption?
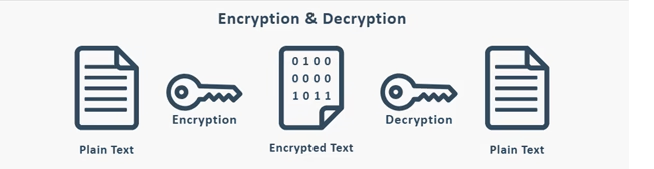
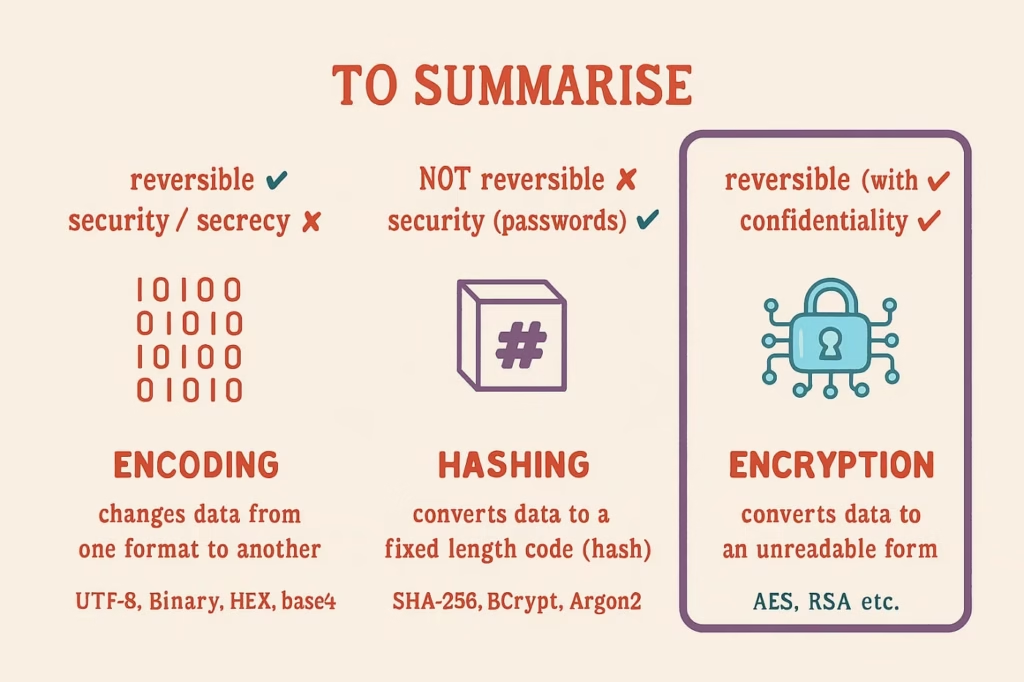
Encryption is the process of converting readable data into an unreadable format to protect it from unauthorised access.
Encrypted data:
- Can be reversed
- Requires a key to be decrypted
- Is used when data needs to be protected but later accessed
Simple definition:
Encryption protects data by locking it with a key so only authorised users can unlock it.
Where Encryption Is Used
Encryption is commonly used to protect:
- Data stored in databases or files
- Data sent over networks
- Sensitive business information
In Microsoft environments, encryption helps ensure:
- Confidentiality of data
- Protection against data exposure
- Compliance with security standards
SC-900 focuses on why encryption exists, not how to configure it.
What Is Hashing?
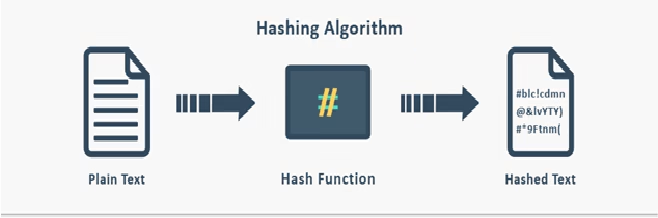
Hashing is the process of converting data into a fixed-length value that cannot be reversed.
Hashed data:
- Cannot be decrypted
- Always produces the same output for the same input
- Is used for verification, not recovery
Simple definition:
Hashing protects data by converting it into a unique fingerprint that cannot be turned back into the original value.
Where Hashing Is Used
Hashing is commonly used for:
- Password storage
- Integrity checks
- Verifying that data has not been changed
Instead of storing actual passwords, systems store hashed values, which improves security even if data is exposed.
SC-900 expects you to understand that hashing is one-way, unlike encryption.
Key Differences Between Encryption and Hashing
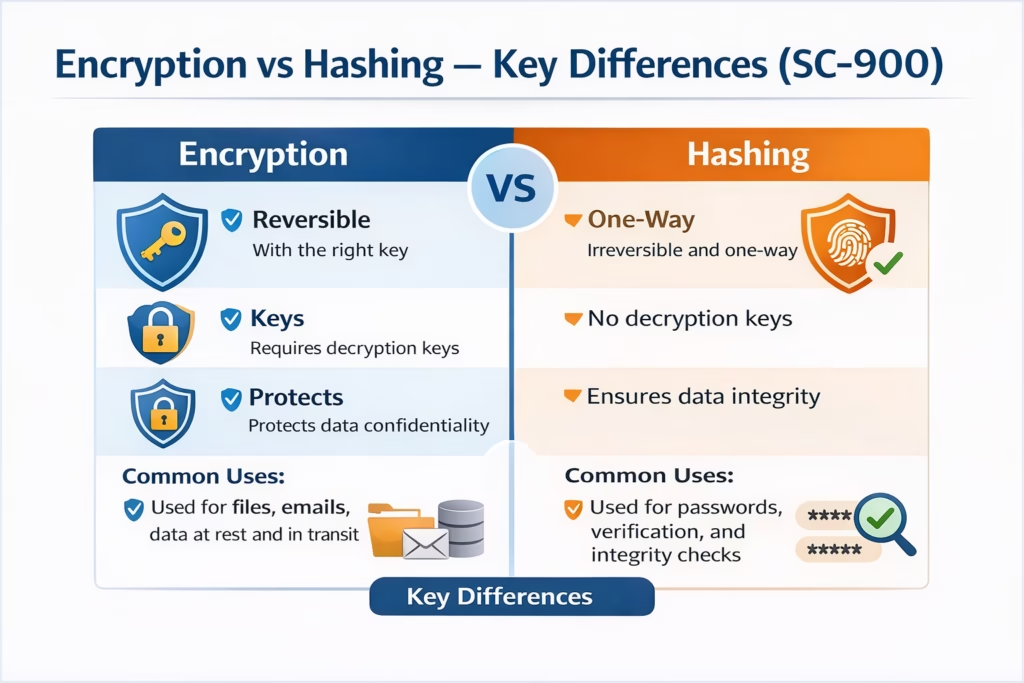
| Feature | Encryption | Hashing |
|---|---|---|
| Reversible | Yes (with key) | No |
| Purpose | Protect data confidentiality | Verify data integrity |
| Uses keys | Yes | No |
| Used for passwords | ❌ No | ✅ Yes |
| Used for data storage | ✅ Yes | ❌ No |
This comparison is exam-critical for SC-900.
Encryption vs Hashing: Simple Example
Encryption example:
A file is encrypted so only authorised users can open and read it later.
Hashing example:
A password is hashed so the system can verify it without ever knowing the original password.
SC-900 tests whether you can recognise which approach is appropriate in each scenario.
Why Hashing Is Not Used to Protect Files
A common beginner mistake is thinking hashing can protect files.
It cannot.
Once data is hashed:
- It cannot be recovered
- It cannot be read again
This is why hashing is used for verification, not for storing retrievable data.
SC-900 often uses this distinction in exam questions.
How Encryption and Hashing Support Security Together
Encryption and hashing are not competing technologies.
They work together to support:
- Confidentiality
- Integrity
- Secure authentication
- Compliance requirements
For example:
- Passwords are hashed
- Files and emails are encrypted
- Integrity checks ensure data has not been altered
SC-900 introduces these ideas to help you understand how data protection works at a high level.
Common Misconceptions SC-900 Helps Clear
SC-900 corrects several misunderstandings:
- “Encryption and hashing are the same.”
They serve different purposes. - “Passwords should be encrypted.”
Passwords should be hashed. - “Hashing protects data from being read later.”
Hashing is irreversible.
Understanding these distinctions is essential for the exam.
Why This Topic Matters Beyond the Exam
Encryption and hashing are not just exam topics.
They are used every day in:
- Identity systems
- Cloud platforms
- Compliance frameworks
- Security policies
SC-900 ensures learners build correct mental models early, before moving into advanced security roles.
SC-900 Exam Tip
For SC-900:
- Remember encryption = reversible
- Remember hashing = one-way
- Know when each is used
- Avoid thinking in terms of algorithms or configuration
If you can explain the difference in simple words, you’re exam-ready.
Final Thoughts: Different Tools for Different Goals
Encryption and hashing solve different security problems.
- Encryption protects data that must be accessed later
- Hashing verifies data without exposing it
SC-900 teaches this distinction to help learners understand how modern security protects information correctly.
Also, view our detailed guide on what is SC-900 to understand Microsoft Security, Compliance, and Identity fundamentals
For official and up-to-date exam objectives, learning paths, and reference material, refer to Microsoft Learn’s SC-900 documentation.
What’s Next in the SC-900 Series
In the next post, we’ll cover:
Governance, Risk, and Compliance (GRC) Fundamentals in SC-900