Privileged Identity Management in SC-900 explains why standing administrative access is a security risk and how organisations control privileged roles using time-bound, just-in-time access.
In many environments, users are granted permanent admin roles “just in case.” Over time, this creates standing privilege, one of the biggest contributors to security breaches.
That’s why Privileged Identity Management (PIM) is a key concept in SC-900 (Microsoft Security, Compliance, and Identity Fundamentals).
SC-900 introduces PIM to explain why privileged access must be controlled, time-bound, and reviewed, not permanently assigned.
What is Privileged Identity Management in SC-900
Most attacks don’t start with full admin access.
They become dangerous when compromised accounts already have elevated privileges.
Common problems include:
- Permanent admin assignments
- Unused privileged roles
- Lack of visibility into who has high-level access
- No approval or review process
SC-900 includes PIM to help learners understand how organisations reduce risk around privileged access.
What Is Privileged Identity Management (PIM)?
Privileged Identity Management (PIM) is an identity governance concept that:
Controls, limits, and monitors privileged access to critical resources.
Instead of granting permanent admin access, PIM promotes:
- Just-in-time (JIT) access
- Approval-based elevation
- Time-bound privileges
- Visibility and accountability
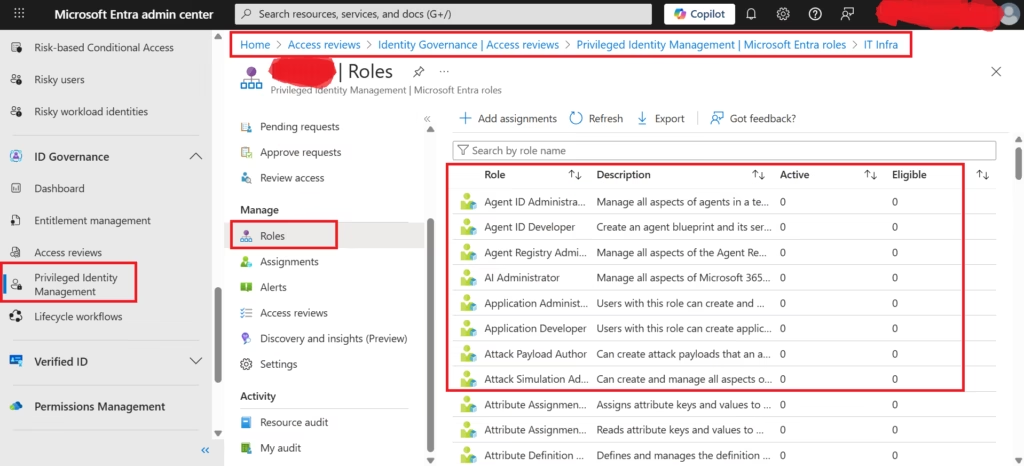
Fig: Privileged Identity Management in Microsoft Entra ID showing eligible and active administrative roles with no standing privileged access.
Viewed Privileged Identity Management roles in Microsoft Entra ID and observed the separation between Eligible and Active role assignments. No active privileged roles were present, which is expected in environments where admin access is not permanently assigned.
What Is Standing Privileged Access?
Standing access means:
- A user is always an administrator
- Privileged roles are active 24/7
- No additional verification is required
This is risky because:
- Compromised accounts immediately gain full control
- Privileged actions are harder to audit
- Mistakes have larger impact
SC-900 highlights standing access as a security anti-pattern.
How PIM Reduces Privileged Access Risk
PIM reduces risk by changing how privileged access is granted.
Key ideas introduced in SC-900:
- Eligible access instead of permanent access
- Activation required before using admin privileges
- Time limits on elevated roles
- Auditable elevation events
In simple terms:
Admin access exists only when needed.
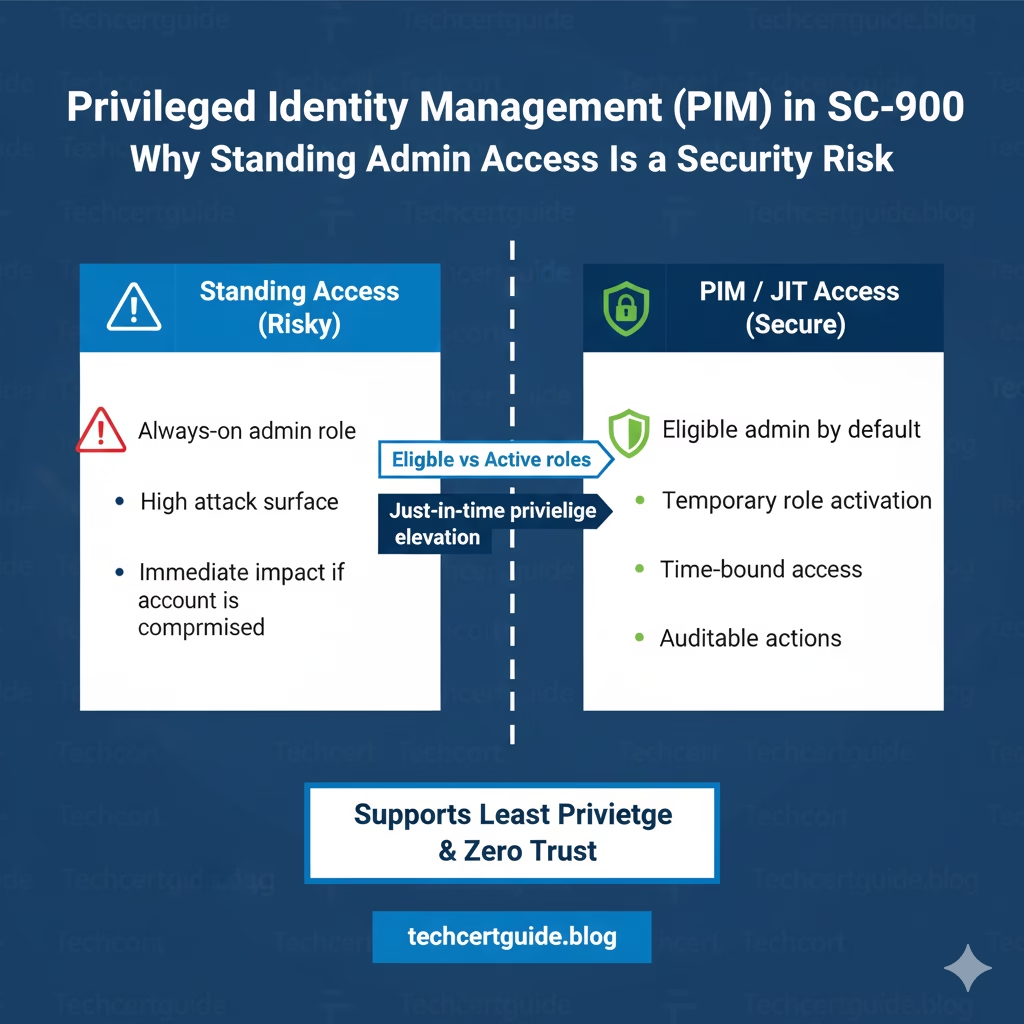
Eligible vs Active Roles (SC-900 Concept)
SC-900 introduces an important distinction:
- Eligible role → User can become an admin
- Active role → User is currently an admin
Most of the time, users remain eligible, not active.
This significantly reduces the attack surface.
PIM and Least Privilege
PIM directly supports Least Privilege Access.
Instead of:
- Always-on admin roles
PIM enables:
- Minimal access by default
- Temporary elevation only when required
SC-900 connects PIM with Least Privilege to reinforce modern access control principles.
PIM and Zero Trust
Zero Trust assumes:
- No implicit trust
- Continuous verification
- Access should be limited and contextual
PIM aligns with Zero Trust by:
- Removing permanent trust
- Requiring explicit activation
- Limiting duration of privileged access
This conceptual connection is exam-relevant.
PIM vs Regular RBAC (Important Difference)
RBAC defines what a role can do.
PIM controls when and how that role can be used.
- RBAC = structure of access
- PIM = governance of privileged access
SC-900 expects learners to understand that PIM complements RBAC, not replaces it.
Why PIM Matters for Governance and Compliance
From a GRC perspective, PIM:
- Reduces audit findings
- Improves accountability
- Provides visibility into admin usage
- Supports separation of duties
Auditors often ask:
Who has admin access, and when was it used?
PIM helps answer that clearly.
What SC-900 Does NOT Expect You to Know About PIM
SC-900 does not require:
- Role activation steps
- Portal configuration
- Approval workflows
- PowerShell commands
The exam tests understanding of why PIM exists, not how to set it up.
Common Misconceptions About PIM
SC-900 helps correct these myths:
- “Admins need permanent access.”
Admin access should be temporary. - “PIM slows down work.”
It reduces risk while maintaining control. - “PIM replaces RBAC.”
PIM works with RBAC.
SC-900 Exam Tip
For SC-900:
- Understand why standing admin access is risky
- Know what eligible vs active means
- Link PIM to Least Privilege and Zero Trust
- Avoid thinking in implementation terms
If you can explain PIM in simple words, you’re exam-ready.
Final Thoughts: Privilege Should Be Earned, Not Permanent
High privileges require high control.
By replacing permanent admin access with controlled, time-bound elevation, organisations dramatically reduce risk without blocking productivity.
SC-900 introduces Privileged Identity Management to ensure learners understand that secure environments treat admin access as temporary, visible, and accountable.
Also, view our detailed guide on what is SC-900 to understand Microsoft Security, Compliance, and Identity fundamentals.
For official and up-to-date exam objectives, learning paths, and reference material, refer to Microsoft Learn’s SC-900 documentation.
What’s Next in the SC-900 Series
Next, we’ll move into Microsoft security tooling with:
Microsoft Defender Overview in SC-900: How Threat Protection Fits Together